LincAccess Software User Manual
Table of Contents
I. Overview
II. Configuration of the Penetrated Machine
- Linux System
- Windows System
III. Configuration of the Penetrating Machine
- Windows System
IV. Common Issues and Solutions
I. Overview
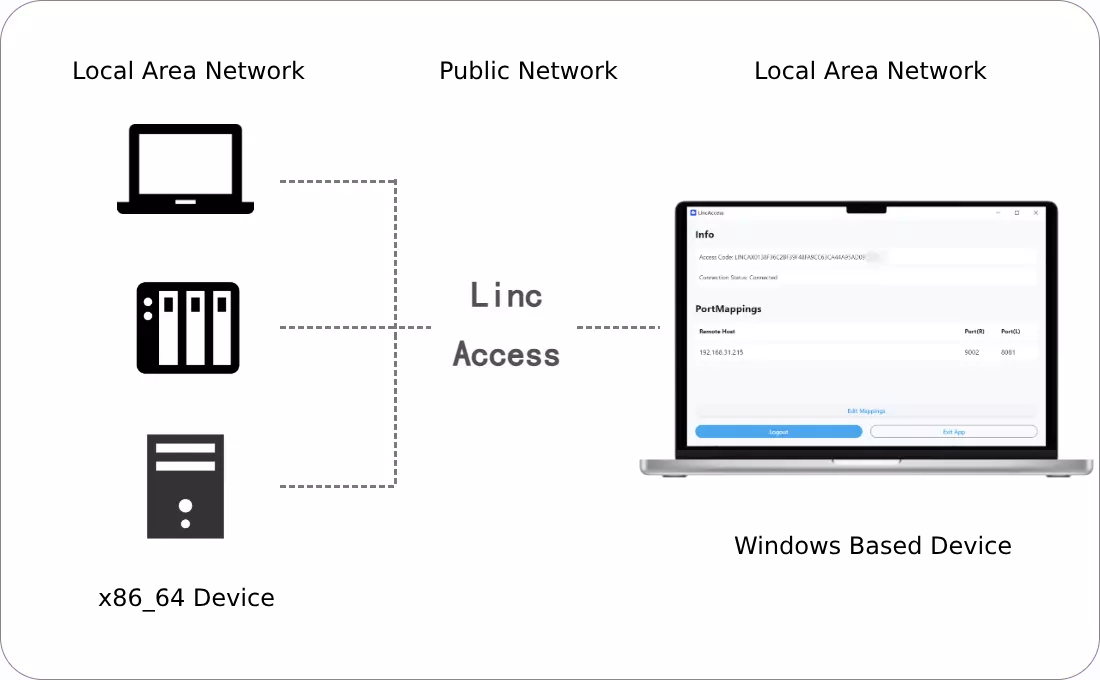
LincAccess is a reverse proxy-based software designed to enable remote access to intranet devices. This software allows easy access to intranet resources without complex network configuration. This document provides first-time users with detailed installation and operational guidance.
II. Configuration of the Penetrated Machine
The penetrated machine refers to the device you wish to access remotely via LincAccess. Configuration steps for Linux and Windows systems are outlined below.
Linux System
1. Install Docker and Configure Docker Image Acceleration Address
Docker is the foundational environment for running LincAccess containers. Ensure Docker is installed on your Linux system. Refer to the following link for installation:
Debian-based systems:
https://docs.docker.com/engine/install/debian/
Verify Docker functionality:
Execute the command:
BASH
docker pull hello-world
Using default tag: latest
latest: Pulling from library/hello-world
c1ec31eb5944: Pull complete
Digest: sha256:305243c734571da2d100c8c8b3c3167a098cab6049c9a5b066b6021a60fcb966
Status: Downloaded newer image for hello-world:latest
docker.io/library/hello-world:latest
If Pull complete appears, Docker is successfully installed.
2. Pull Image and Run Container
- Pull LincAccess image using Docker:
BASH
docker pull kriswhale/linc-access-app:[version]
Find the latest version at: https://hub.docker.com/r/kriswhale/linc-access-app/tags
- Run the container:
BASH
docker run -dp 8099:80 --name linc-access-app kriswhale/linc-access-app:[version]
8099is the host port mapping (modifiable as needed)-p 8099:80maps host port 8099 to container port 80
3. Access Container via Browser
- On any browser-enabled device, visit:
http://[Penetrated_Machine_IP]:[Port_Number]
Example: If IP is
192.168.31.100and port is8099, visit:http://192.168.31.100:8099
- Enter correct credentials and set a pairing code (access credential). Securely store this code:
- LincAccess Account: Your account
- LincAccess Password: Your password
- Pairing Code: Custom verification code (confidential access credential)
Windows System
1.Windows server configuration method 1 (available for Linux and Windows)
(1)Install Docker
- Download Docker Desktop for Windows: https://www.docker.com/products/docker-desktop
- Follow prompts to install and launch Docker Desktop.
- Verify Docker functionality:
POWERSHELL
docker pull hello-world
Sample output:
TEXTUsing default tag: latest
latest: Pulling from library/hello-world
c1ec31eb5944: Pull complete
Digest: sha256:305243c734571da2d100c8c8b3c3167a098cab6049c9a5b066b6021a60fcb966
Status: Downloaded newer image for hello-world:latest
docker.io/library/hello-world:latest
If Pull complete appears, Docker is functional.

(2)Pull Image and Run Container
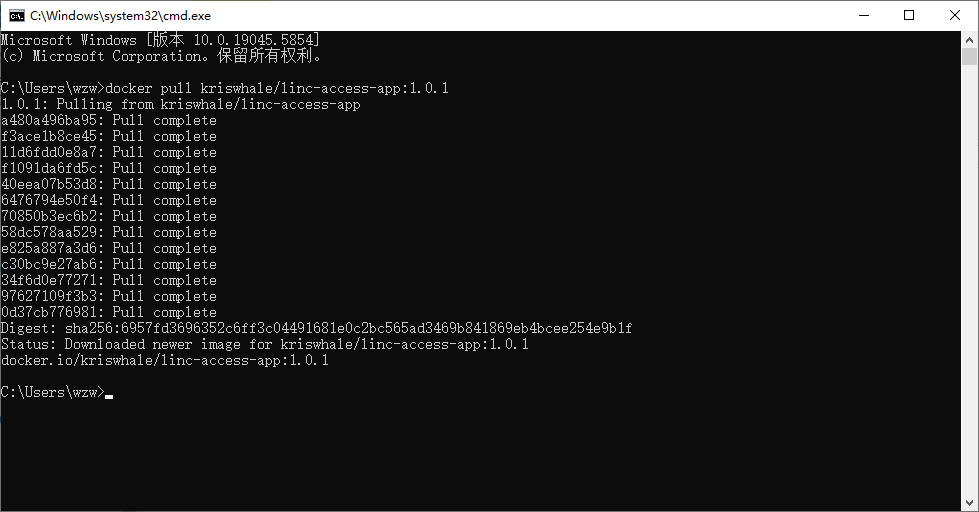
- Open PowerShell/Command Prompt and pull the image:
POWERSHELL
docker pull kriswhale/linc-access-app:[version]
Find latest version at: https://hub.docker.com/r/kriswhale/linc-access-app/tags
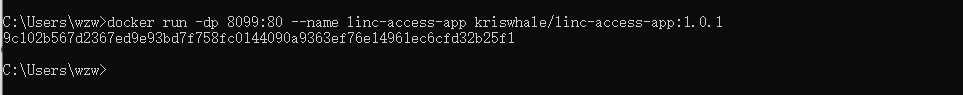
- Run the container:
POWERSHELL
docker run -dp 8099:80 --name linc-access-app kriswhale/linc-access-app:[version]
8099 maps to container port 80 (modifiable). Access via `localhost:8099
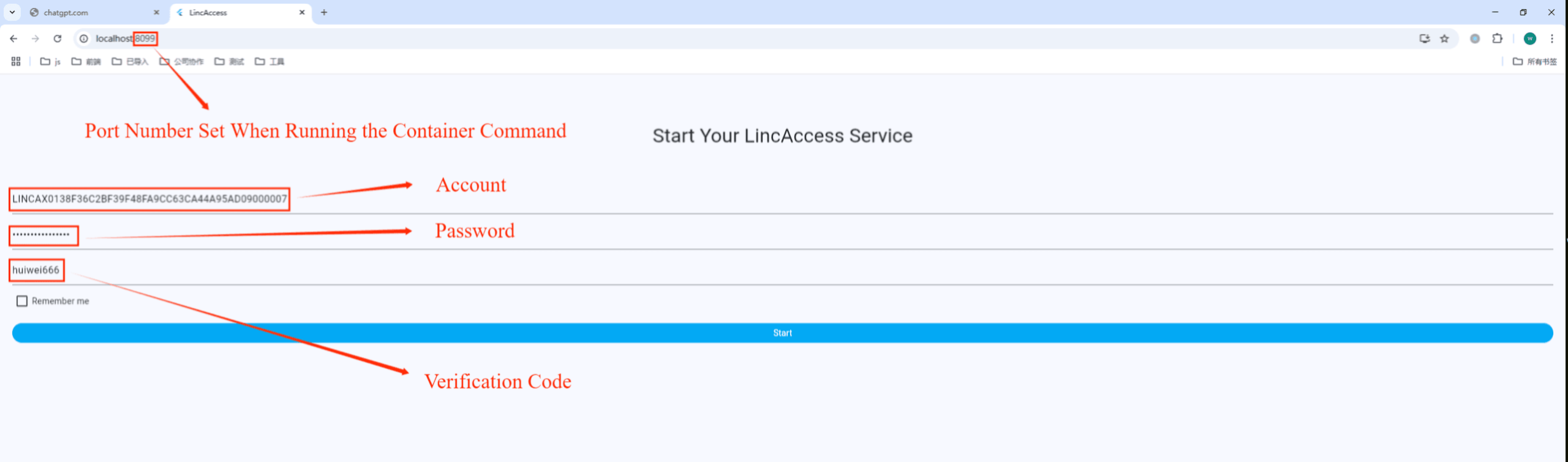
(3) Access Container via Browser
- On the local machine, visit:
http://127.0.0.1:[Port_Number]
Example: Port
8099→http://localhost:8099
Enter credentials and pairing code:
- LincAccess Account: Your account
- LincAccess Password: Your password
- Pairing Code: Verification code (confidential)
2. Windows server configuration method 2(Only available on windows)
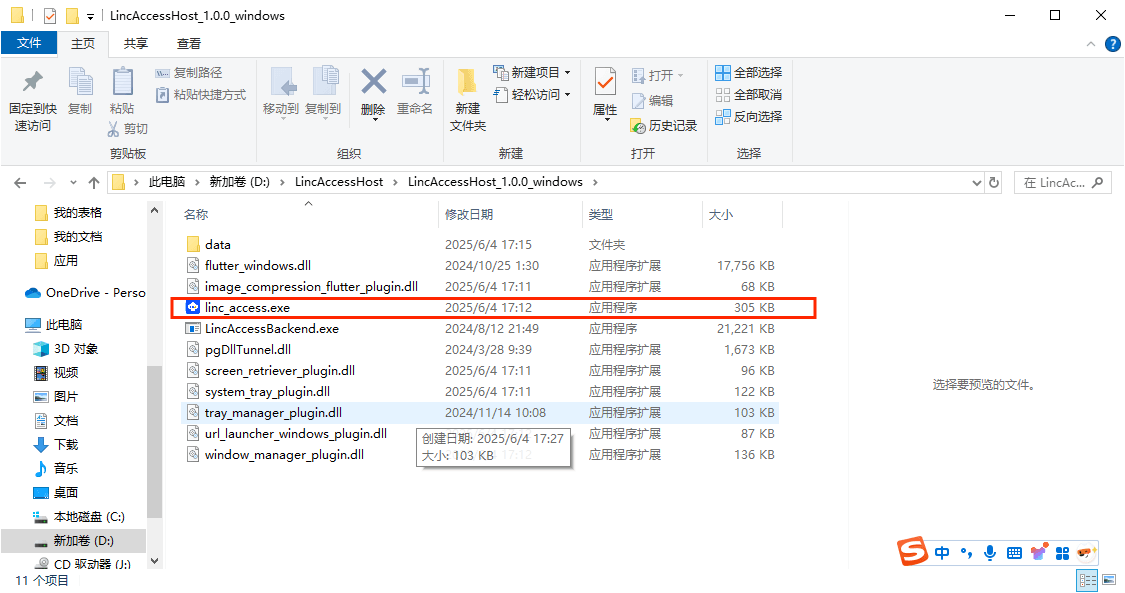
(1)Download, install, and launch linc_access.exe:
- Open the webpage: https://www.lincos.ai/en/lincaccess-download/, and click to download LincAccessHost (Windows Version)
- Once the ZIP package is downloaded, extract its contents.
- Double-click
linc_access.exeto launch
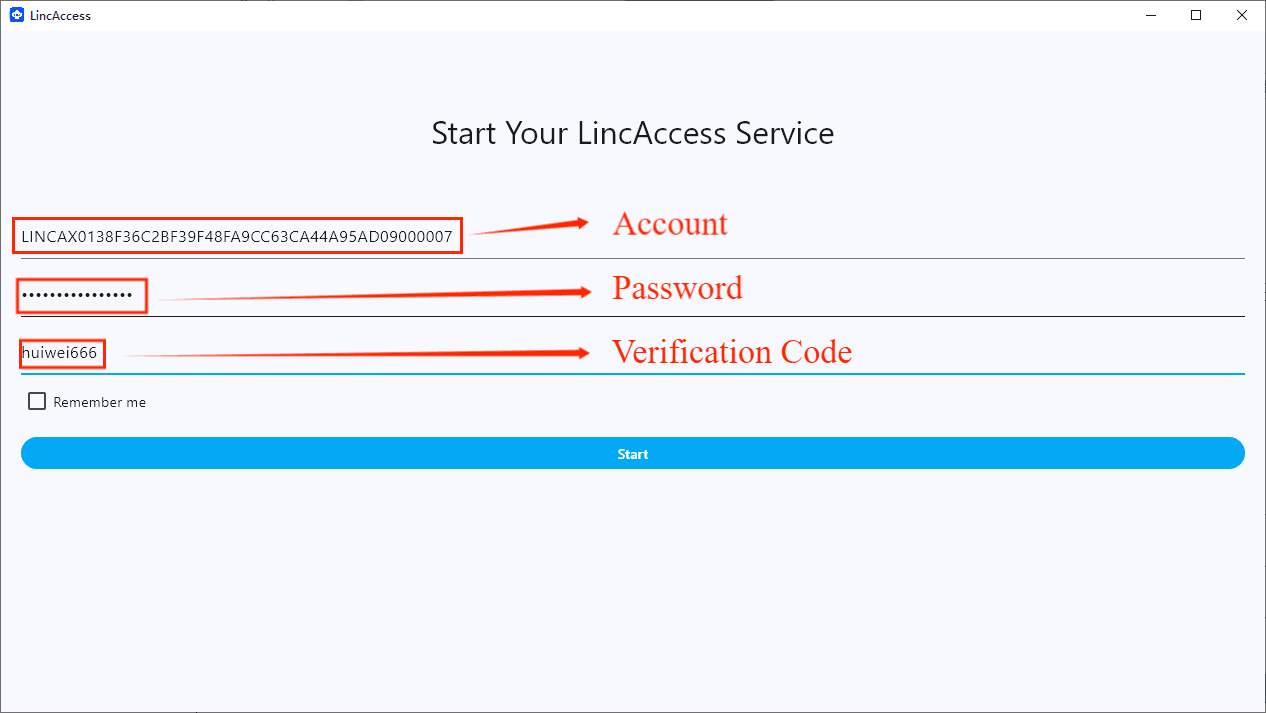
(2)Enter credentials and pairing code:
- LincAccess Account: Your account
- LincAccess Password: Your password
- Pairing Code: Verification code (confidential)
III. Configuration of the Penetrating Machine
The penetrating machine refers to the device used for remote access. Configuration steps for Windows are below.
Windows System
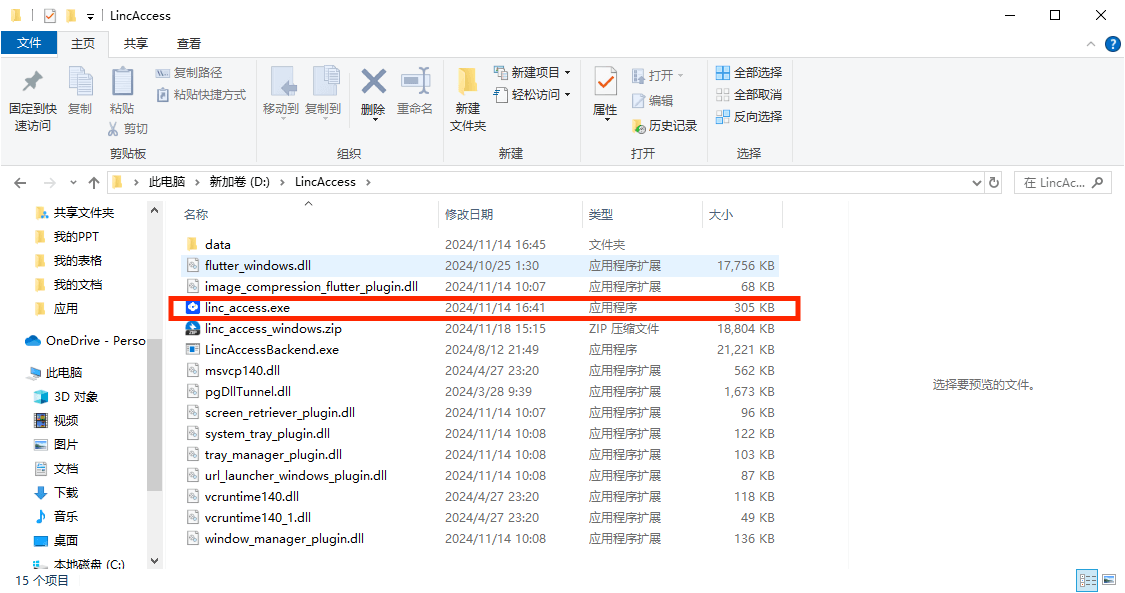
Download, install, and launch linc_access.exe:
- Open the webpage: https://www.lincos.ai/en/lincaccess-download/, and click to download LincAccess (Windows Version).
- Once the ZIP package is downloaded, extract its contents.
- Double-click
linc_access.exeto launch
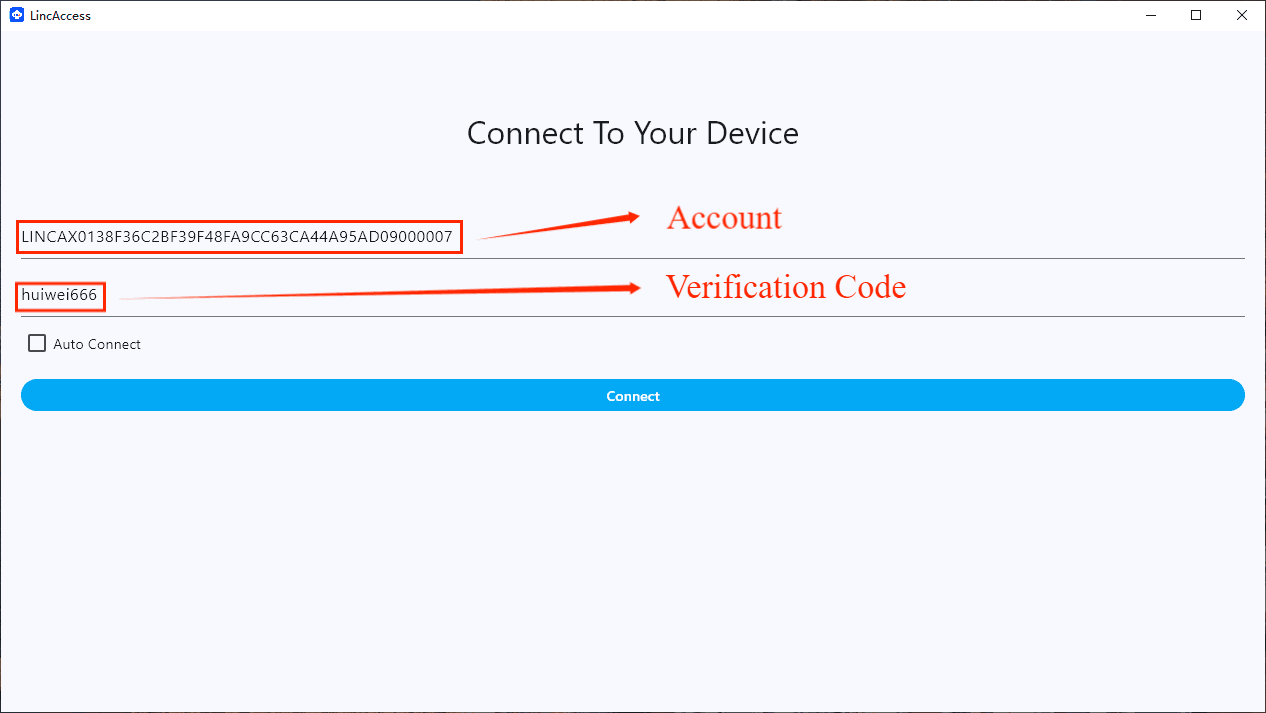
2. Enter Credentials
In the main interface:
- Enter your LincAccess account
- Enter the pairing code configured on the penetrated machine
Click Connect to log in
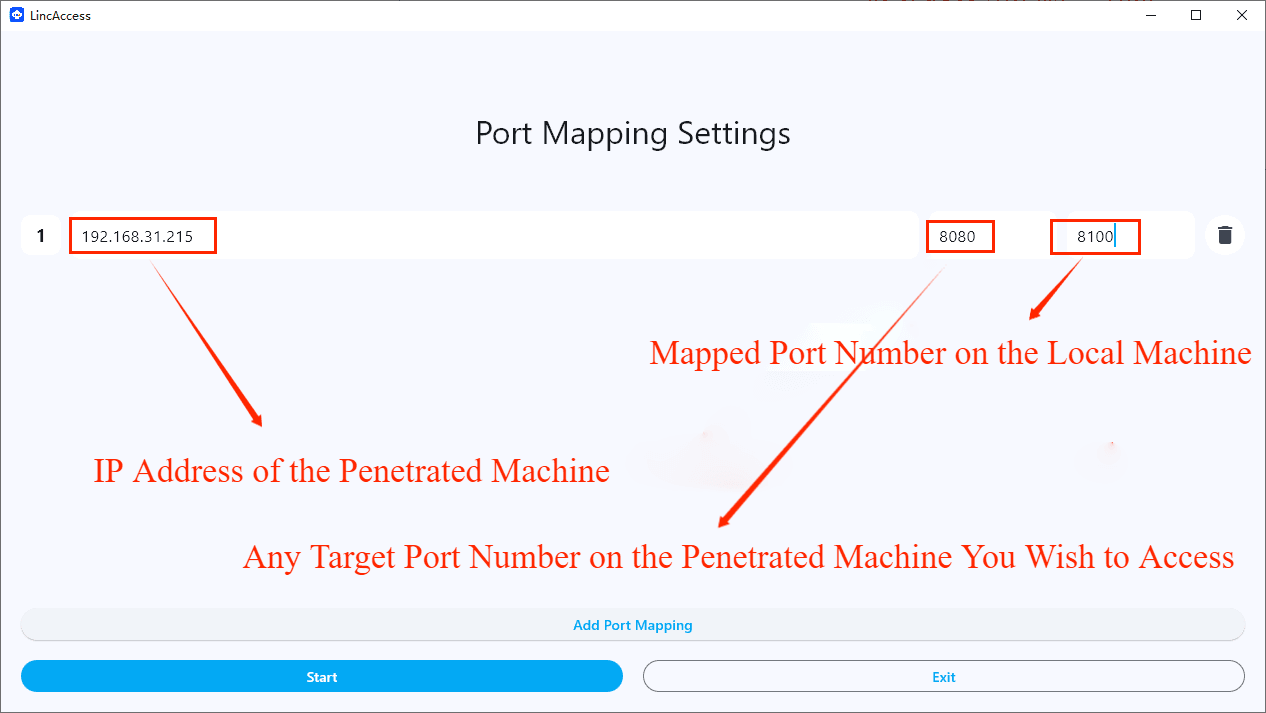
3. Add Port Mapping
Click Add Port Mapping and configure:
- Remote Host: IP of penetrated machine (e.g.,
192.168.31.100) - Remote Port: Target port on penetrated machine (e.g.,
8080) - Local Port: Mapping port on local machine (e.g.,
8100)
- Remote Host: IP of penetrated machine (e.g.,
Click Start to activate mapping
4. Access Remote Resources
Open browser and visit:
http://127.0.0.1:[Local_Port]
Example: Local port
8100→http://127.0.0.1:8100

IV. Common Issues and Solutions
1. Browser cannot access container page:
Verify container status:
BASH docker psEnsure port isn't occupied by other services
2. Docker service fails to start:
- Check system compatibility. Upgrade OS or use VM if unsupported
3. Windows client login failure:
- Verify account/pairing code accuracy
4. Port mapping fails to access resources:
- Confirm firewall rules allow port access on penetrated machine